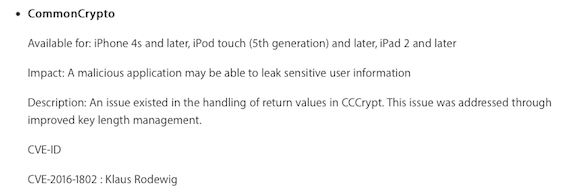
Until macOS 10.11.4 and iOS 9.3.1 CommonCrypto/corecrypto supported Blowfish operations with key sizes longer than 448 bits. Starting with macOS 10.11.5 and iOS 9.3.2 this is no longer the case: the minimum and maximum key sizes are now enforced (respectively kCCKeySizeMinBlowfish 8 bytes and kCCKeySizeMaxBlowfish 56 bytes).
- Easily preview Mermaid diagrams
- Live update when editing
- Capture screenshots
- Create PNG from the Terminal
- Free download on the Mac App Store
If you perform a Blowfish operation with a key length longer than 448 bits, it will now fail with an error kCCParamError. Below is an example of code using a 64 bytes Blowfish key that works on macOS 10.11.4 / iOS 9.3.1 but returns an error kCCParamError on newer systems:
#import <Foundation/Foundation.h>
#import <CommonCrypto/CommonCrypto.h>
int main(int argc, const char * argv[])
{
@autoreleasepool
{
uint8_t keyData[64] =
{
0x00, 0x11, 0x22, 0x33, 0x44, 0x55, 0x66, 0x77, 0x88, 0x99, 0xAA, 0xBB, 0xCC, 0xDD, 0xEE, 0xFF,
0x00, 0x11, 0x22, 0x33, 0x44, 0x55, 0x66, 0x77, 0x88, 0x99, 0xAA, 0xBB, 0xCC, 0xDD, 0xEE, 0xFF,
0x00, 0x11, 0x22, 0x33, 0x44, 0x55, 0x66, 0x77, 0x88, 0x99, 0xAA, 0xBB, 0xCC, 0xDD, 0xEE, 0xFF,
0x00, 0x11, 0x22, 0x33, 0x44, 0x55, 0x66, 0x77, 0x88, 0x99, 0xAA, 0xBB, 0xCC, 0xDD, 0xEE, 0xFF
};
CCCryptorRef cryptorRef;
CCCryptorStatus status = CCCryptorCreate(kCCDecrypt, kCCAlgorithmBlowfish, 0, keyData, sizeof(keyData), NULL, &cryptorRef);
NSLog(@"CCCryptorCreate result: %d", status);
if(status != kCCSuccess)
{
NSLog(@"*** CCCryptorCreate failed!!!");
}
}
return 0;
}
If you have to support Blowfish with a key longer than 448 bits, you can’t use anymore CommonCrypto and should switch to a different implementation. Note that using Blowfish with a key longer than 448 bits is not recommended as it weakens the security guaranteed by the algorithm.